BTQ Technologies launched a Bitcoin Quantum testnet on Jan. 12, 2026 to experiment with post-quantum signatures in a Bitcoin-like environment. The network swaps Bitcoin’s current signature primitive for ML-DSA, a module-lattice scheme standardized by NIST as FIPS 204, and is intended as a sandbox for measuring operational trade-offs without changing mainnet governance. The testnet supports wallet creation, signing, verification and mining so engineers can observe practical impacts on blockspace and tooling.
Introduction to BTQ’s Bitcoin Quantum Testnet
The testnet’s core purpose is to trial post-quantum signatures and see how they behave under real Bitcoin-like conditions. By replacing ECDSA/Schnorr with ML-DSA, BTQ makes the protocol-level consequences visible, from transaction size to block limits. This approach is meant to inform engineers and implementers rather than to propose an immediate mainnet switch; it provides a controlled setting for coordination and performance testing. For context on broader ecosystem responses, see the discussion of overall blockchain reaction in related coverage: blockchain reaction.
Quantum Threats to Bitcoin
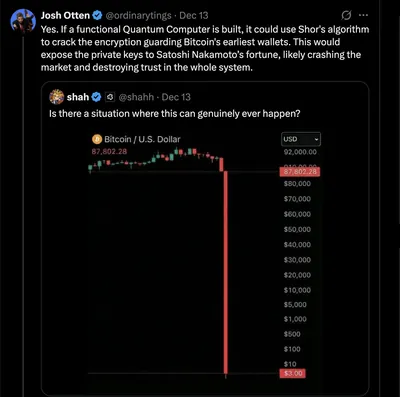
Most quantum-threat discussions for Bitcoin center on digital signatures and onchain public-key exposure rather than on coin supply or random wallet guessing. The theoretical mechanism is Shor’s algorithm, which could let a sufficiently capable quantum computer derive private keys from visible public keys and thus produce valid signatures. That creates two practical exposure modes: long-range risk where public keys are already onchain, and short-range risk when keys are revealed during a pending spend. Current hardware does not present an immediate break, but the threat model is straightforward to describe.
Engineering Challenges of Post-Quantum Signatures
Replacing elliptic-curve signatures with post-quantum schemes changes many engineering assumptions because ML-DSA signatures are roughly 38–72 times larger than typical ECDSA signatures. To accommodate that extra data, BTQ’s testnet raises the block size limit to 64 mebibytes (MiB), showing how signature size flows through to blockspace, bandwidth and verification costs. Running a full lifecycle — from wallet creation to mining — lets teams see real verification and propagation impacts rather than relying solely on paper estimates.
Old BTC Risk: Legacy Output Types
When analysts discuss “old BTC” risk they usually mean coins whose public keys are already visible onchain, because those keys could be targeted if a cryptographically relevant quantum computer existed. The output types that directly place elliptic-curve public keys in the locking script are Pay-to-Public-Key (P2PK), Pay-to-Multi-Signature (P2MS) and Pay-to-Taproot (P2TR). These legacy forms concentrate exposure differently by count and by value.
- P2PK is a very small share of UTXOs (about 0.025%) but holds a large share of BTC value: roughly 8.68% or 1,720,747 BTC, much of it long-dormant.
- P2MS and P2TR also expose public keys by design; address reuse can turn otherwise brief spend-time exposure into long-range exposure because public keys remain visible once onchain.
BTQ highlights this exposed-key framing and cites a figure of 6.26 million BTC as potentially exposed when measuring public-key visibility across historic outputs. That is part of why BTQ argues practical testnets are useful now: to quantify the operational costs of protecting or migrating those coins.
Mitigation Strategies for Bitcoin
At a protocol level, preparedness conversations split into two tracks: first, reducing structural exposure in existing script designs; second, evaluating specific post-quantum signature schemes and their costs. A recent example aiming at the first track is BIP 360, which proposes Pay-to-Tapscript-Hash (P2TSH) — a Taproot-like output that removes the key-path spend to avoid relying on elliptic-curve signatures. Related “hash-only” or script-spend constructions, sometimes framed as Pay-to-Quantum-Resistant-Hash (P2QRH), pursue the same avoidance of onchain public keys.
Those proposals emphasize incremental, coordination-heavy change rather than an immediate algorithm swap, since any migration affects blockspace and requires tooling and social agreement. For more on post-quantum standards and protocol-level responses, see coverage of post-quantum work in the ecosystem: post-quantum standards.
Conclusion: BTQ’s Contribution to Quantum Preparedness
BTQ’s Bitcoin Quantum testnet does not prove imminent breakage, but it makes two things clear: the dominant threat model is tied to exposed public keys, and moving to post-quantum signatures is primarily an engineering and coordination challenge. By adopting ML-DSA and increasing the block limit, the testnet exposes concrete trade-offs that any future migration would face. As a sandbox, it helps quantify costs and inform incremental mitigation choices rather than prescribing a single path forward.
Why this matters
If you mine or hold Bitcoin, the core point to watch is whether your coins’ outputs reveal public keys onchain. Coins with exposed public keys are the ones that quantum-capable adversaries would target in the threat model described by BTQ and others. Even if widespread quantum attacks remain theoretical today, understanding which outputs carry long-range exposure helps prioritize which holdings and practices need attention.
What to do?
For a miner with between 1 and 1000 devices operating in Russia, practical short-term steps are simple and do not require protocol changes. First, avoid address reuse and prefer outputs that do not place public keys onchain when possible; this reduces long-range exposure in the basic threat model. Second, monitor developer discussions and wallet updates about BIP 360/P2TSH and related approaches so you can act if migration tools become available.
Finally, for operational safety, keep node and wallet software updated and consider segregating long-term dormant funds from actively used mining payouts until migration guidance is clear. These steps help reduce personal exposure without assuming any immediate quantum break.